ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Security Failure Analysis
Explore photoemission and thermal laser stimulation techniques.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Malevolent Code Analysis
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Security Labs
Governmental agencies
Academics
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
Introducing esReverse 2024.01 — for Binary Security Analysis
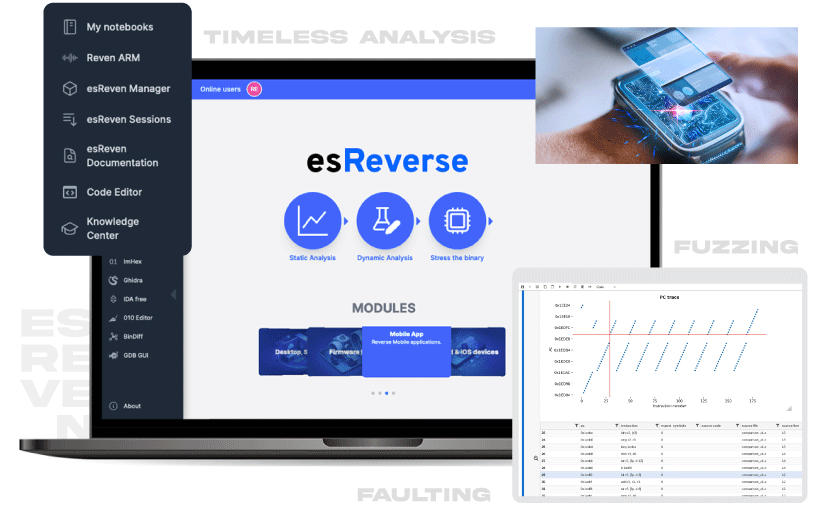
We are thrilled to unveil esReverse, eShard's cutting-edge platform dedicated to binary security analysis. esReverse offers a comprehensive environment for software binary analysis that seamlessly integrates static, dynamic, and stress testing capabilities.
More than a tool, esReverse changes the way the binary analysis expertise is developed by reconciling techniques, supporting collaborative work and empowering experts with a totally flexible platform. esReverse sets a new standard, not only by facilitating but by accelerating the enhancement of critical binary analysis capabilities in teams of experts.

esReverse core platform is a web-based application that requires no local installation, making it effortlessly accessible from any device with a web browser. Tailored to meet the stringent requirements of top-secret organizations, esReverse is flexible by design, allowing seamless integration across diverse IT infrastructures. Whether deployed on air-gapped, on-premises systems or extended through cloud services, esReverse adapts to the specific needs of your operational environment, ensuring uncompromised security and adaptability.
By integrating JupyterLab with its notebook functionality, all team members share the same platform for their individual or collaborating analysis work. It offers a stable and mature environment to make effective collaboration and to develop the internal expertise. Acting as a hub for cutting-edge tools from the research community, esReverse enables users to organize their binary analysis tasks, share insights, and easily revisit their work. This platform not only streamlines collaboration but also serves as a foundation for accumulating and accessing collective knowledge and innovation.
➕ Extensions
esReverse extensions for Intel, ARM or RISC-V focuses on providing unparalleled emulation capabilities for covering many dynamic analyses: code profiling, fault injection, dynamic fuzzing or even timeless analysis.
Through its extensions and the experience in Reven technology, esReverse offers a comprehensive array of options for emulating:
- a full Intel x86, x64 system, facilitating the execution of any Windows or Linux operating system.
- ARM binary, enabling the emulation of IoT firmware, or systems such as Android for kernel investigation or mobile application,
- RISC-V binary, enabling the emulation of IoT firmware.
This offers the opportunity to implement sophisticated binary analysis and combine them:
Validate codes against fault injections or fuzzing:
Inheriting years of practical experience in hardware physical attacks, esReverse introduces sophisticated fault injection features designed to rigorously test binaries and confirm the effectiveness of their protections. This flexible and high-performance tool enables code validation and thorough investigation into the robustness of security measures embedded within binary code. Furthermore, esReverse facilitates pre-production testing through the creation of targeted fault campaigns and seamless integration of scripts into CI/CD pipelines, embodying a proactive DevSecOps approach.
Maintaining its commitment to an open platform philosophy, esReverse enables the orchestration of fuzzing campaigns that merge binary emulation with renowned tools like AFL++ or Boofuzz, or even with custom-built frameworks. Once initiated, the platform excels in overseeing the exploration of potential vulnerabilities revealed through suspicious crash scenarios. This is achieved by leveraging in-depth code coverage analysis and the innovative approach of timeless analysis, making esReverse an indispensable asset for comprehensive security assessments.
esReven technology for Timeless Analysis:
esReverse Timeless Analysis allows thorough examination of system execution (CPU, Memory, Hardware Events). Analysts can scrutinize, rewind, and track execution to comprehend behavior, diagnose issues, or analyze flow without real-time operation constraints. The feature is available for Intel and ARM softwares.
esReverse Data Tainting for Intel binaries enables tracking data flow to identify how "tainted" data can impact program execution, aiding in the discovery of vulnerabilities such as security breaches or bugs. By marking inputs as tainted and observing their propagation, taint analysis ensures secure handling of sensitive data and prevents untrusted data from infiltrating critical system components.
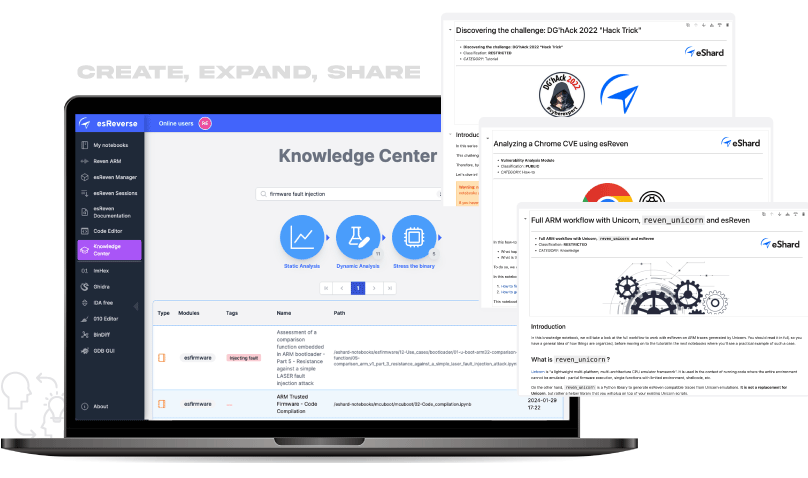
Expertise Modules extensions
Recognizing the gap between theoretical knowledge and practical application, eShard experts continuously craft expertise material to transfer knowledge and expertise in the complex field of binary analysis. These modules encapsulate years of R&D through comprehensive catalogs of examples and techniques, both explained and implemented, alongside reference binaries or traces. Designed to be both a knowledge hub and a practical toolkit, our technical content not only provides deep insights but is also ready to be applied directly to your setup, bridging the gap between reading and doing.
In summary, esReverse strives to be the ultimate toolbox for security analysts, seamlessly combining technology and expertise into a collaborative platform.
Explore more on our website or reach out to us to experience the power of esReverse firsthand.

