ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Photoemission Analysis
Detect photon emissions from your IC to observe its behavior during operation.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Code Audit & Verification
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Automotive
Security Lab
Gov. Agencies
Academics
Defense
Healthcare
Energy
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
eShard releases a new Expertise Module for Post-Quantum Cryptography
Post-Quantum Cryptography has gained substantial momentum in recent months. Tension has been steadily building as the NIST selection process for final algorithms progresses and ended up with a first selection. The stakes are high, as this marks the dawn of a new era in public key cryptography, anticipating the substantial leap in computational capabilities with quantum computer technologies.
As a result, various algorithms have emerged, including CRYSTALS-Kyber, CRYSTALS-Dilithium, Falcon, and SPHINCS+.
CRYSTALS-Kyber is a Key Encapsulation Mechanism (KEM) to allow key sharing, while CRYSTALS-Dilithium, Falcon and SPHINCS+ are designed for digital signature. The algorithms are not stand-alone primitives, but designed as protocols, focusing them on specific cryptographic tasks. The process is still ongoing, with the most recent NIST recommendations being issued in August 2023.
All selected algorithms are built upon robust mathematical foundations, including lattices or hash trees. The technical community has not only emphasized the mathematical strengths of these algorithms but has also scrutinized potential vulnerabilities in their implementation. Particular attention has been given to physical attacks, including side-channel and fault injection, opening up new avenues of investigation for specialists in the field.
As a result, developers and experts must stay aligned with ongoing research. The selection of the right implementation has become crucial for many organizations. This necessitates swiftly gaining expertise in comprehending the new algorithms and their variations, understanding attack vectors and trends, and ultimately making informed implementation choices that align with the capabilities of the final devices.
How to secure your Post-Quantum Cryptography implementations?
To make the right decisions, many stakeholders must make sure to develop the expertise in-house. The topic is too critical to outsource the decisions that will have impacts for many years. It is with this mindset that eShard developed a dedicated base of theoretical and practical knowledge in a new PQC module with several objectives.
What does this release provide? The first objective is to provide essential knowledge for understanding these new algorithms. This begins with foundational elements to grasp their mathematical construction, including descriptions of the fundamental mathematical concepts essential for understanding the implementation. For each algorithm, we offer a 'simplified' Python implementation to elucidate their operational principles.
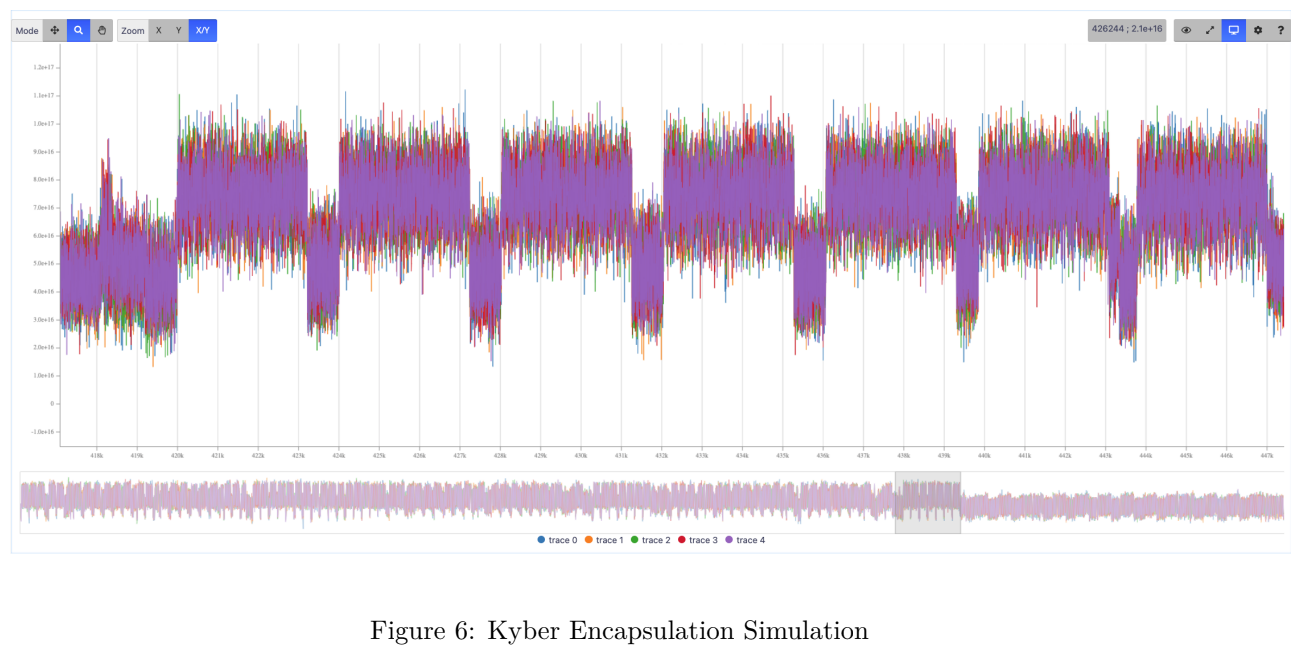
Secondly, the module incorporates various datasets to offer experts reference materials for conducting attacks and making refinements. Our approach was to generate datasets that are highly exploitable, as they result from emulating compiled PQC reference codes. Consequently, they provide an accurate representation of data involved in code execution. Some of the traces represent many millions of points. This is properly managed by eShard’s visualizer for smooth usage.
Last, but certainly not least, key recovery attacks and leakage analyses were concurrently developed. This involved a careful selection of side-channel attacks from a wealth of publications in the field. To enhance the technical precision, eShard's specialists collaborated closely with globally recognized experts from PQShield to fine-tune this selection. The objective was to create detailed technical explanations of how these attacks operate and offer a guided script for implementing these techniques consecutively.
In this emerging field of cryptography, maintaining the integrity and delivering best-in-class technical material is essential. To accomplish this, the insight of a reliable external partner is invaluable. Consequently, we capitalize on the unparalleled expertise of PQShield, granting them early access to our technical content. This collaboration enabled us to refine our material, enhancing its overall quality.
And the result represents a unique source of technical material for anyone willing to build in-house expertise in the complex field of strong Post Quantum Cryptography:
- The mathematical knowledge for understanding the new algorithms concepts
- The data sets for experimenting the security analyses
- The attack techniques and leakage analyses for developing the in-house expertise and challenging existing implementations.
From day 1, the PQC module can be delivered to any users of the esDynamic platform. It therefore takes benefit of the key features that have made its success in the community of experts: open, flexible and collaborative. All the technical contents provided in this module aimed at helping our customers to manage their internal expertise and reaching a good level of know-how in the field of PQC secure implementation.

This release does not aim at being static. It will be upgraded regularly following the developments in this fast moving space. The current version is making a strong focus on CRYSTALS-Kyber. The next release will go deeper in the CRYSTALS-Dilithium algorithm.
Ready to secure your future in the post-quantum world? Contact us now to explore how our PQC solutions can empower your cybersecurity strategy.
