ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Security Failure Analysis
Explore photoemission and thermal laser stimulation techniques.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Malevolent Code Analysis
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Security Labs
Governmental agencies
Academics
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
Scared: open source side-channel library by eShard
In short: eShard recently released Scared, a new open source Python library for side-channel attacks. Scared is a professional side-channel framework with easy-to-use APIs and great performance to run side-channel analyses. Try it on Binder!
During CHES 2019 conference in Atlanta, eShard presented its newly released open source library for side-channel attacks named Scared.
With Scared, our goal is to provide a professional open source side-channel framework for people to develop their side-channel projects
Where does Scared come from?
eShard is a technology company specialized in the security of embedded and connected devices. Our flagship product, esDynamic, is a data science platform dedicated to the security of embedded systems. The platform integrates Python libraries for side-channel analysis, white box cryptography testing and hardware fault injections.
We have developed esDynamic with the philosophy to empower the experts. Leveraging the latest data sciences technologies, esDynamic is now a comprehensive scientific platform to apply and expand expertise in cryptography, side-channel analysis and hardware fault injections. esDynamic platform developed by eShard.
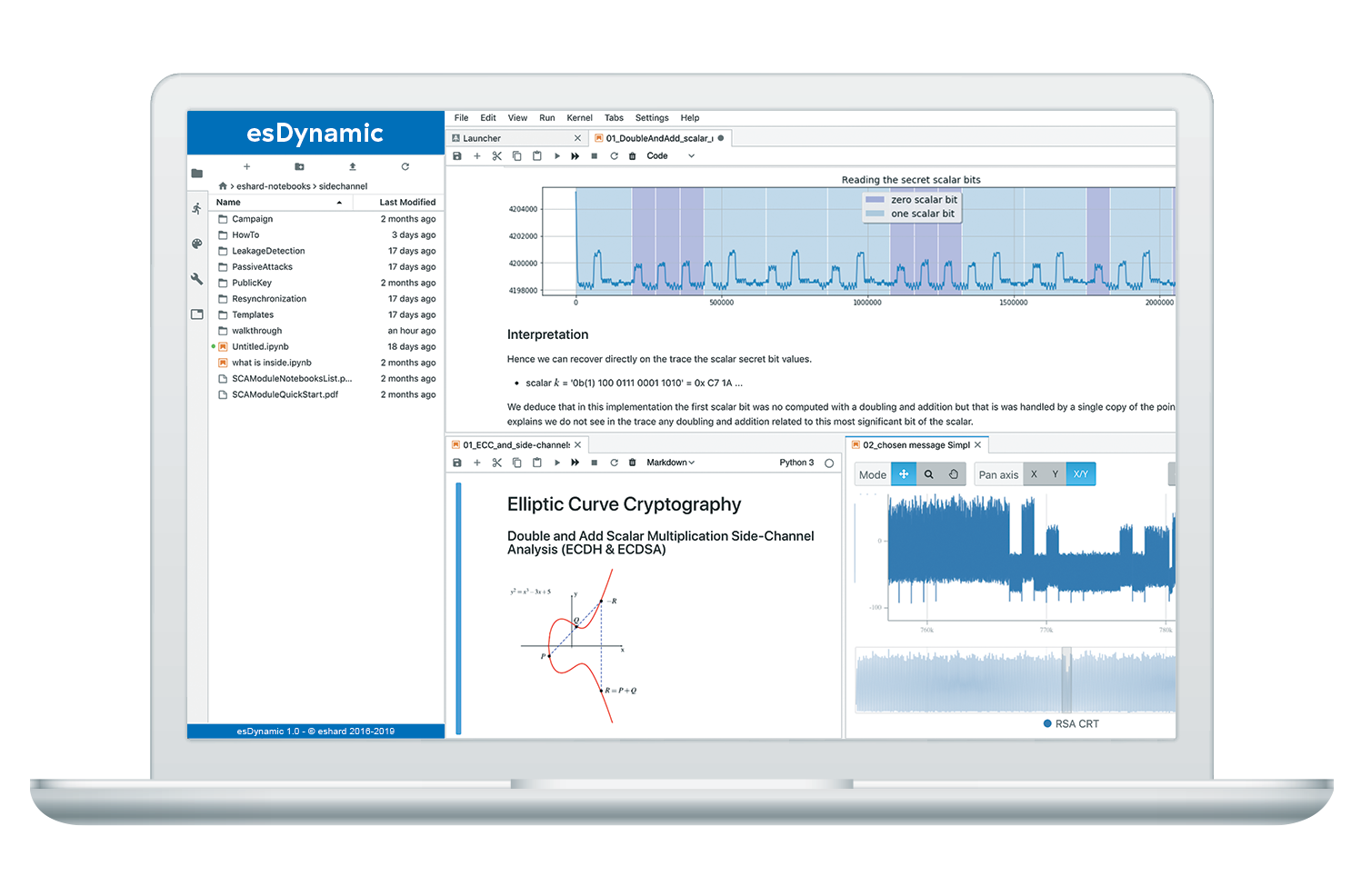 esDynamic platform developed by eShard
esDynamic platform developed by eShard
esDynamic offers an open environment for the experts to work and develop their expertise. As the experts have control, it is natural to give access to the code of the core Python modules of the platform. Therefore, after 3 years of development, we think it is a good time to release our base side-channel library as open source and make it available to everybody.
By doing so, we are also happy to share our knowledge and expertise in side-channel attacks and to provide a professional open source side-channel framework to help people build their side-channel analysis projects.
What is inside
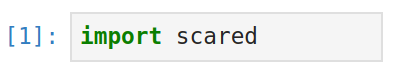
Scared is a Python library composed of the core components of our commercial side-channel software, minus the advanced features developed by eShard such as interactive widgets, traces visualizer, advanced results display, Python notebooks etc.
Still, Scared contains all the features needed to perform side-channel analyses. The library is composed of the following functionalities.
Unified side-channel traces representation

Scared provides a unibold textfied way to manipulate trace sets independently of the underlying data set formats. The implementation is based on abstract reader methods and a unified set of APIs. Using this abstract reader design, Scared virtually supports any type of trace format.
The data set abstraction is provided by the THS (Trace Header Set) object and its APIs. The library includes reader APIs for the most common side-channel trace formats, including eShard’s trace set format (.ets) which we believe is quite efficient to perform side-channel analysis. Besides, using the abstract reader methods, the user can easily integrate in the framework his own custom trace format when needed.
Pre-processing methods
 Pre-processing methods are available to apply different types of data processing on the traces before the attacks. The provided methods include standard signal processing techniques such as the Fast Fourier Transform as well as processing methods dedicated to high-order attacks such as the Centered Product transformation. Again, to ensure flexibility, the user can easily integrate his own processing methods which can be used during the attacks.
Pre-processing methods are available to apply different types of data processing on the traces before the attacks. The provided methods include standard signal processing techniques such as the Fast Fourier Transform as well as processing methods dedicated to high-order attacks such as the Centered Product transformation. Again, to ensure flexibility, the user can easily integrate his own processing methods which can be used during the attacks.
Cryptographic targets and selection functions
 The library integrates common cryptographic targets such as AES and DES. To define what part of the algorithm to attack, we provide a set of selection functions corresponding to the most common targeted intermediate values. The user can easily implement and use custom selections functions to attack different intermediate values or different algorithms.
The library integrates common cryptographic targets such as AES and DES. To define what part of the algorithm to attack, we provide a set of selection functions corresponding to the most common targeted intermediate values. The user can easily implement and use custom selections functions to attack different intermediate values or different algorithms.
Analysis methods

The library provides an analysis module to perform side-channel analysis with different types of distinguishers. We have implemented most of the state-of-the-art side-channel distinguishers such as DPA, CPA, MIA, T-Test, but also ANOVA, NICV and Template attacks. The attacks can be performed using different leakages models and different types of score discriminant.
APIs design
All the features are accessible through user-friendly high level APIs. Our objective is to simplify the process of running side-channel attacks to let the user focus on the most important parts of side-channel testing which are the attack strategy and results analysis. The high-level APIs also offer an easy learning curve for new users and beginners in side-channel.
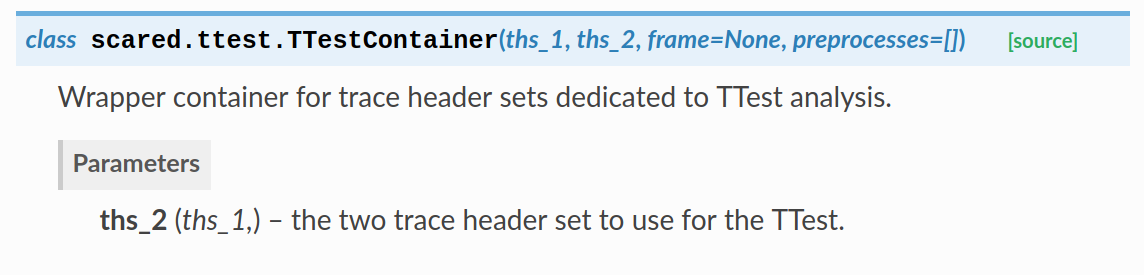 Example of API description from Scared documentation
Example of API description from Scared documentation
For users willing to run more complex analyses, we provide several low-level APIs which are extendable and composable so that the user can easily build custom analysis processes.
All the APIs are described in the online Scared documentation available here.
Methodology
To develop Scared, our team follows the same methodology as for the development of our commercial modules. For the development, we focus on 3 key points:
-
Performance: as side channel analysis requires to process huge amount of data, we put a special focus on code optimization in order to speed up the attacks execution.
-
Quality: our team is composed of software engineers and experts in side channel attacks working together to provide to the user the best in terms of APIs design and code quality.
-
Documentation: Scared comes with a complete documentation describing the APIs of the library as well as a series of examples.
Scared is meant to be a living project. We will keep updating the code in the future and contributions to the project are welcome. We would like that the project evolves based on the community’s needs and ideas.
In a few lines
In a few lines of code, this is how you can start to use Scared.
Load data set
After importing Scared, we can start by loading a data set. In the example below, we open a subset of the DPA v2 contest composed of 20,000 traces. The traces and metadata (plaintexts, ciphertexts etc) are accessible via the Trace Header Set object.
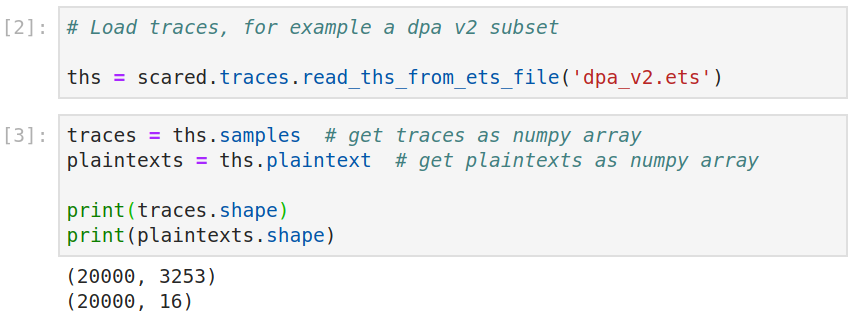
Define target
To run an attack, we first need to define what part of the cryptographic algorithm we want to target. This is done by choosing a selection function. Below, to attack the DPA v2 trace set we will target the delta between the two last rounds of the AES.
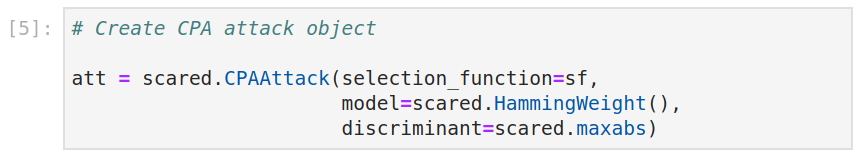
Create attack object
We can then define our attack object. Below, we define a Hamming Weight CPA attack.
Run the attack
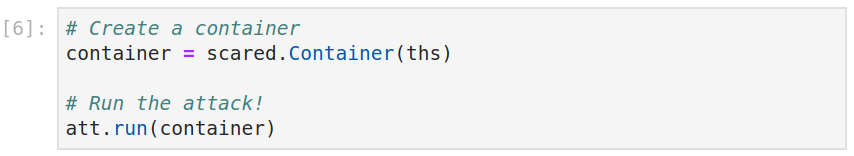
Before running the attack, one needs to build a Container encapsulating our data set. Finally, one can run the attack by simply calling the .run() method.
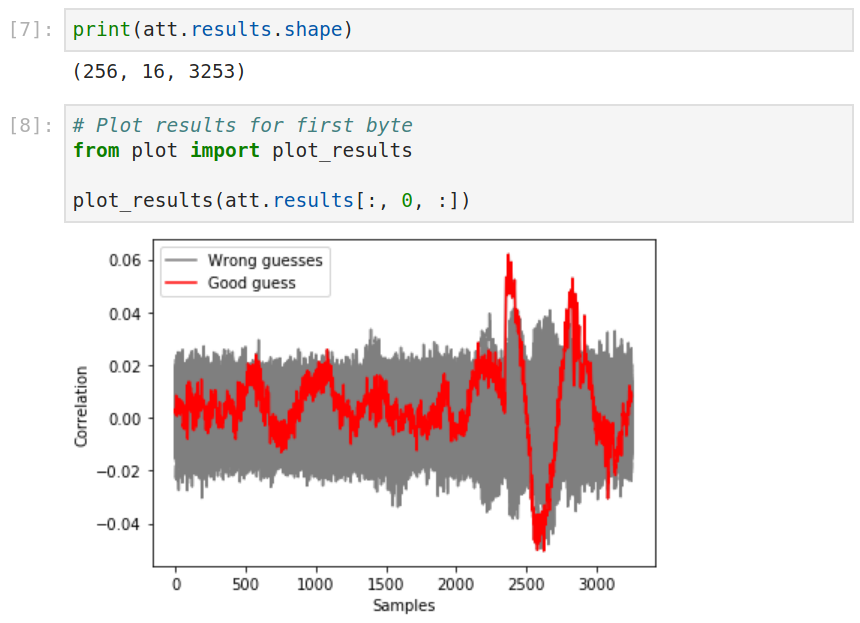
The results of the attack are stored in the attack object as a Numpy array.
Benchmark
We have decided to benchmark Scared in order to provide information about where the library stands in terms of performance.
Very few references can be found on the performance of side channel tools, so we based our benchmark on the main available work, which is the open source benchmark performed by Ilya Kizhvatov and Cees-Bart Breunesse available [here](We have decided to benchmark Scared in order to provide information about where the library stands in terms of performance.
Very few references can be found on the performance of side channel tools, so we based our benchmark on the main available work, which is the open source benchmark performed by Ilya Kizhvatov and Cees-Bart Breunesse available here. In this work, they compare the performance of 4 side-channel frameworks: ChipWhisperer, Daredevil, Inspector and Jlsca.). In this work, they compare the performance of 4 side-channel frameworks: ChipWhisperer, Daredevil, Inspector and Jlsca.
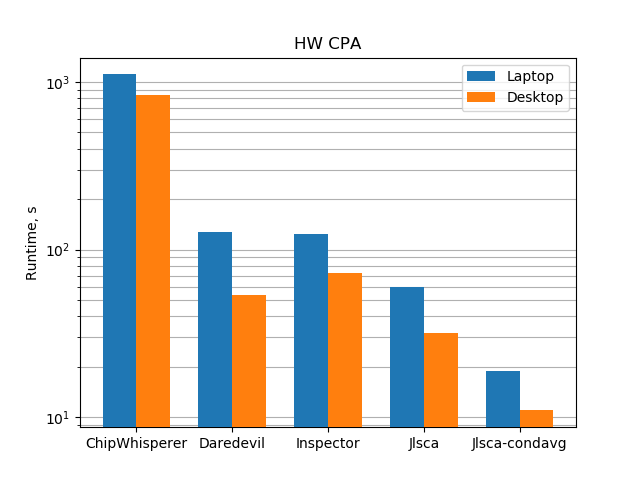 Results of the original benchmark performed by Ilya Kizhvatov and Cees-Bart Breunesse
Results of the original benchmark performed by Ilya Kizhvatov and Cees-Bart Breunesse
We extended this original benchmark to include the performance of two new side channel frameworks, namely LASCAR from Ledger Donjon, and Scared from eShard.
To provide fair comparisons, we ran this extended benchmark in the same conditions as the original benchmark. We used the same benchmark test which is a Hamming Weight CPA on 100,000 traces of 512 float32 samples. We also used a desktop configuration equivalent to the original benchmark configuration. Below we provide the results of our extended benchmark.
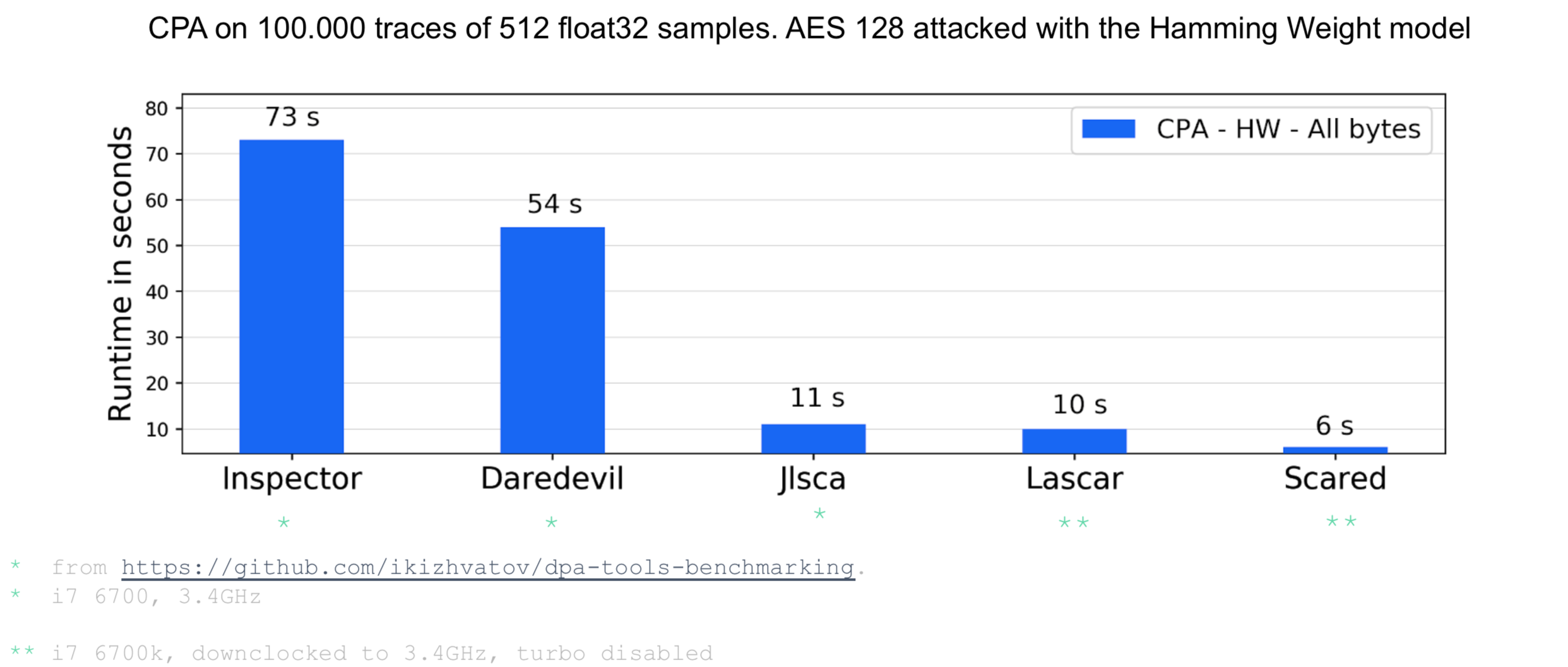 Results of extended benchmark by eShard
Results of extended benchmark by eShard
As we can see from the results, Scared is the best-in-class side-channel framework in terms of performance. As previously mentioned, our team focuses on code optimization in order to provide a fast framework able to run large analyses efficiently.
Get started
The source code of Scared is available on both GitLab and GitHub.
Scared can easily be installed with pip:
pip install scared
or conda:
conda install -c eshard scared
We recommend using Scared in a notebook environment such as Jupyter. We have set up a notebooks repository to provide examples and tutorials for the library. The notebooks from the repository can easily be executed in an online Jupyter environment using Binder. Click here to launch a Binder instance with the Scared notebooks and library already integrated.


To get started, you can have a look to the introduction notebook. Click here to directly access this notebook in a Binder instance.
We encourage you to use Scared and hope the library will help you build efficient side-channel analyses.
So don’t be Scared, install the library and have fun :)
Disclaimer
Scared library is licensed under LGPL V3 license.
It is mainly intended for non-commercial use, by academics, students or professionals willing to learn the basics of side-channel analysis. If you wish to use this library in a commercial or industrial context, eShard provides commercial licenses under fees. For more information, contact us!
Acknowledgements
Thanks to Guillaume Bethouart for providing the results of the extended benchmark. Thanks to Aurelien Vasselle for the cover picture. And thanks to Hugues Thiebeauld for proofreading the post.