ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Photoemission Analysis
Detect photon emissions from your IC to observe its behavior during operation.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Code Audit & Verification
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Automotive
Security Lab
Gov. Agencies
Academics
Defense
Healthcare
Energy
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
What’s the difference between WinDBG and esReverse’s Time Travel tool?
Lately, we’ve been hearing the same question from analysts again and again: What’s the difference between WinDBG and the Time Travel feature in esReverse?
Or more directly: Why would you pay for esReverse when WinDBG’s Time Travel Debugging is free?
Fair question.
If you work in vulnerability research or malware analysis, chances are you’ve used WinDBG’s Time Travel Debugging (TTD). It’s a solid tool for tracing user-mode execution, stepping backward through crashes, and digging into application-level bugs. It’s free, well-documented, and deeply integrated into the Windows ecosystem.
So why build something else?
But once your investigation goes beyond a single process, such as, when it spans kernel activity, cross-process behavior, or system-wide effects, you start hitting the limits of what WinDBG can show you.
That’s where esReverse comes in.
In this post, we’ll break down what WinDBG TTD does well, what it doesn’t do, and how esReverse is built for a different kind of job: understanding full systems, not just stepping through code.
Let’s start with the basics.
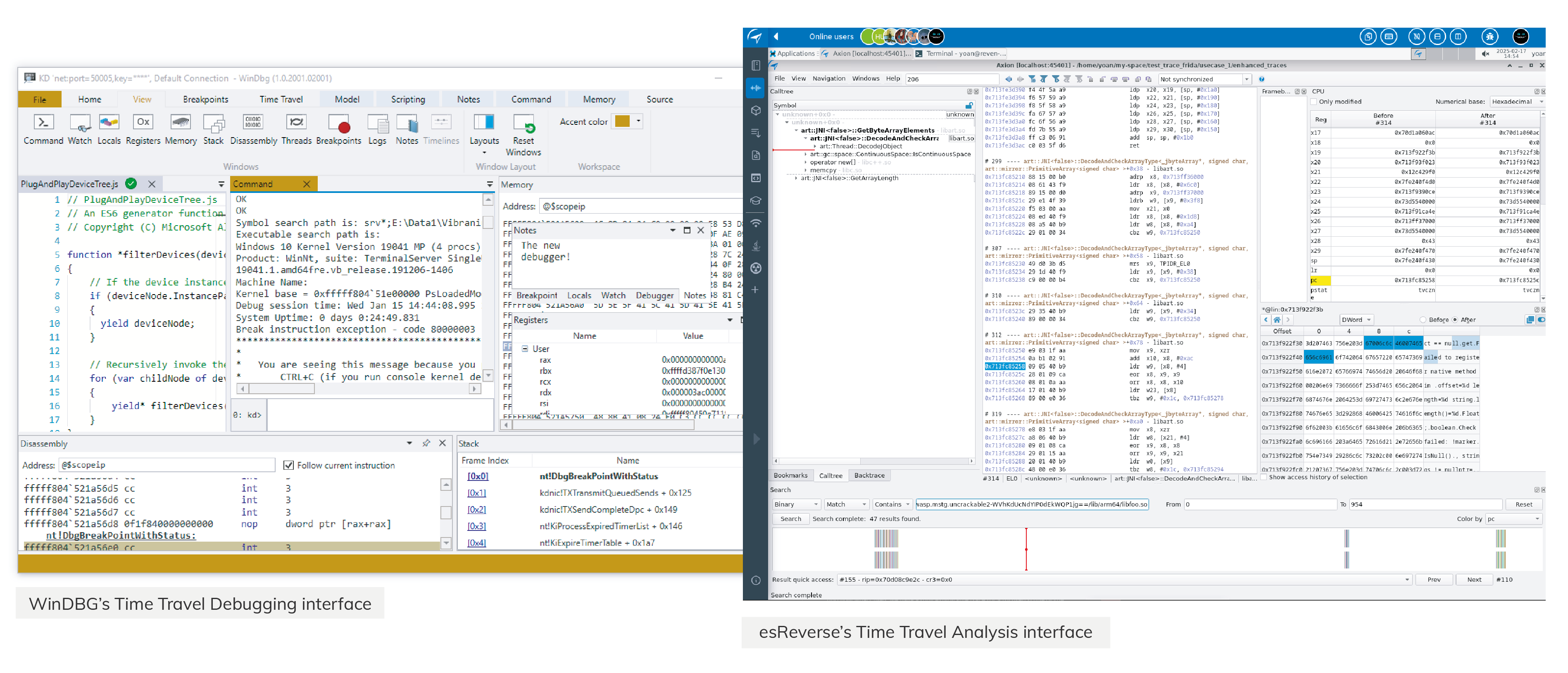
What is WinDBG?
WinDBG (short for Windows Debugger) is Microsoft’s official debugger for Windows. It’s been around for years and is widely used by developers, security researchers, and reverse engineers to inspect and debug code running on Windows.
At its core, WinDBG lets you attach to a process or load a memory dump and walk through the execution flow, setting breakpoints, stepping through instructions, checking registers, viewing memory, and so on. It’s powerful, but not exactly beginner-friendly. Most people using WinDBG already know their way around low-level Windows internals.
To make debugging more flexible, Microsoft introduced Time Travel Debugging (TTD) around 2016. It allows you to record the entire execution of a program and move forward or backward in time, so you can trace exactly how the program got to a certain state.
How does Time Travel Debugging work in WinDBG?
TTD works by recording the execution of a user-mode process into a trace file. This trace captures every instruction the process runs, as well as relevant system state and memory changes. Once the recording is done, you can load it into WinDBG and start navigating the timeline.
You can step through execution forward and backward, pause, inspect memory, and trace how specific values evolved. This is extremely useful when analyzing crashes or subtle logic bugs.
TTD also supports scripting. Using JavaScript, you can automate trace analysis, set conditions, extract insights, or build repeatable workflows.
Limitations of WinDBG’s Time Travel Debugging tool
Despite how useful WinDBG TTD can be, it has clear limitations.
First, it’s limited to user-mode applications. You won’t be able to trace kernel drivers, system calls, or anything happening in kernel space. If you’re trying to follow the path of an exploit that escalates privileges or triggers a kernel crash, you’ll be missing half the story.
Second, it only records what happens inside the target process. So if the application interacts with child processes, injects code elsewhere, modifies the registry through a helper, or relies on any form of inter-process communication, that activity is out of view.
Microsoft also notes that TTD doesn’t work well with protected or security-hardened processes, which may interfere with instrumentation or block trace generation.
For vulnerability research, this means you may only capture the triggering conditions of a bug, not how the system reacts or how an exploit completes.
For malware analysis, you may see a loader in action, but not how it sets up persistence, modifies system state, or passes control to a payload.
WinDBG TTD is a strong debugger. But at the end of the day, it's still a debugger. If you need deeper visibility across time, memory, and system layers, you’ll need something purpose-built for that kind of analysis.
What esReverse adds to the picture
esReverse enables Time Travel Analysis on a full-system emulation. You’re no longer tracing just a single process, you’re analyzing how an entire system behaves over time.
You can boot a full OS, like Windows, Linux, or Android, and move back and forth through its execution. That includes kernel activity, system calls, memory allocations, and interactions between processes. You’re looking at the full picture, not just one piece of it.
That’s especially useful when behavior crosses boundaries. A driver triggers a crash, but the root cause started in userland. A payload appears in memory, but wasn’t written by the process you're debugging. These are the kinds of questions that regular debugging tools struggle to answer.
On Intel platforms, esReverse also supports taint analysis. That lets you follow how a piece of data was created and where it flows, even if it moves between user and kernel space or across multiple threads and processes.
You can automate your analysis with a Python API, generate execution coverage, and connect with other tools like Binary Ninja. Built-in modules let you extract pcap data, view file system events, or search physical memory for access patterns.
Unlike traditional debuggers, esReverse comes with its own GUI designed specifically for this type of analysis.
That’s why we refer to it as Time Travel Analysis, because it goes beyond debugging.
Which tool should you use?
Both WinDBG and esReverse are powerful, but they’re built for different jobs.

If you're debugging a user-mode application and want to step through code to find a bug, WinDBG makes a lot of sense. It’s fast, free, and tightly integrated with Windows development workflows.
But as a security analyst, you want to go deeper; you need to follow how data moves between components, understand kernel behavior, and figure out how a complex exploit works. esReverse gives you access to everything: userland, kernel, inter-process activity, physical memory, and system state over time.
Use WinDBG when you want to debug code. Use esReverse when you need to understand systems.
