ALL-IN-ONE PLATFORM
esDynamic
Manage your attack workflows in a powerful and collaborative platform.
Expertise Modules
Executable catalog of attacks and techniques.
Infrastructure
Integrate your lab equipment and remotely manage your bench.
Lab equipments
Upgrade your lab with the latest hardware technologies.
PHYSICAL ATTACKS
Side Channel Attacks
Evaluate cryptography algorithms from data acquitition to result visualisation.
Fault Injection Attacks
Laser, Electromagnetic or Glitch to exploit a physical disruption.
Photoemission Analysis
Detect photon emissions from your IC to observe its behavior during operation.
EXPERTISE SERVICES
Evaluation Lab
Our team is ready to provide expert analysis of your hardware.
Starter Kits
Build know-how via built-in use cases developed on modern chips.
Cybersecurity Training
Grow expertise with hands-on training modules guided by a coach.
ALL-IN-ONE PLATFORM
esReverse
Static, dynamic and stress testing in a powerful and collaborative platform.
Extension: Intel x86, x64
Dynamic analyses for x86/x64 binaries with dedicated emulation frameworks.
Extension: ARM 32, 64
Dynamic analyses for ARM binaries with dedicated emulation frameworks.
DIFFERENT USAGES
Penetration Testing
Identify and exploit system vulnerabilities in a single platform.
Vulnerability Research
Uncover and address security gaps faster and more efficiently.
Code Audit & Verification
Effectively detect and neutralise harmful software.
Digital Forensics
Collaboratively analyse data to ensure thorough investigation.
EXPERTISE SERVICES
Software Assessment
Our team is ready to provide expert analysis of your binary code.
Cybersecurity training
Grow expertise with hands-on training modules guided by a coach.
INDUSTRIES
Semiconductor
Automotive
Security Lab
Gov. Agencies
Academics
Defense
Healthcare
Energy
ABOUT US
Why eShard?
Our team
Careers
FOLLOW US
Linkedin
Twitter
Youtube
Gitlab
Github
Enhancing Semiconductor Security with Pre-Silicon Testing
Side-channel vulnerabilities are a familiar challenge for hardware manufacturers. Attackers can exploit these weaknesses to bypass traditional security measures by analyzing subtle physical signals, such as power consumption variations, electromagnetic emissions, or timing differences, to extract sensitive data like cryptographic keys without leaving a trace.
The stealthy nature of these attacks forces manufacturers to rethink their security strategies.
![]()
Traditionally, such vulnerabilities were often discovered through “post-silicon testing”, meaning: after a chip was fully built. While this process remains essential for validating a product, it has its limitations. By the time a flaw is detected, companies have already poured millions into development and manufacturing. Fixing the issue often requires costly redesigns, new photomasks, and extended production timelines. This reactive approach, though reliable, leaves little room for flexibility or quick adaptation, especially in the face of side-channel attacks.
Relying solely on post-silicon testing may not be enough to catch these vulnerabilities early. This is where the shift to pre-silicon testing becomes invaluable. Pre-silicon security testing allows chip designers to check their hardware or software IP against side-channel vulnerabilities during the design phases, well before the chip is produced.
Instead of waiting for the physical product to test for weaknesses, pre-silicon tools like Ansys RedHawk-SC Security, with eShard’s side-channel testing tools, simulate real-world side-channel attack scenarios early in the process. This proactive approach doesn’t just save time and money; it ensures that potential vulnerabilities are caught and fixed before they can turn into costly problems down the line.
![]()
A smarter (and more cost-effective) approach
With pre-silicon testing, manufacturers can predict how a chip will behave under various side-channel attack vectors, such as power noise or electromagnetic side-channel emissions.
By integrating Ansys’s physics simulation engines with eShard’s side-channel attack solutions, this collaboration offers a powerful solution that enables designers to secure their chips from the very start. The result? Reduced risk, fewer production setbacks, and stronger, more resilient products hitting the market.
However, this doesn't mean post-silicon testing becomes irrelevant. On the contrary, post-silicon testing remains a crucial step in the verification process. By combining both pre-silicon and post-silicon testing, designers can create a layered security strategy that maximizes protection.
Pre-silicon testing catches potential issues early, while side-channel testing during post-silicon verification ensures the final product can withstand real-world threats. Together, they form a comprehensive, end-to-end security solution that gives manufacturers confidence from the design phase all the way to the final product.
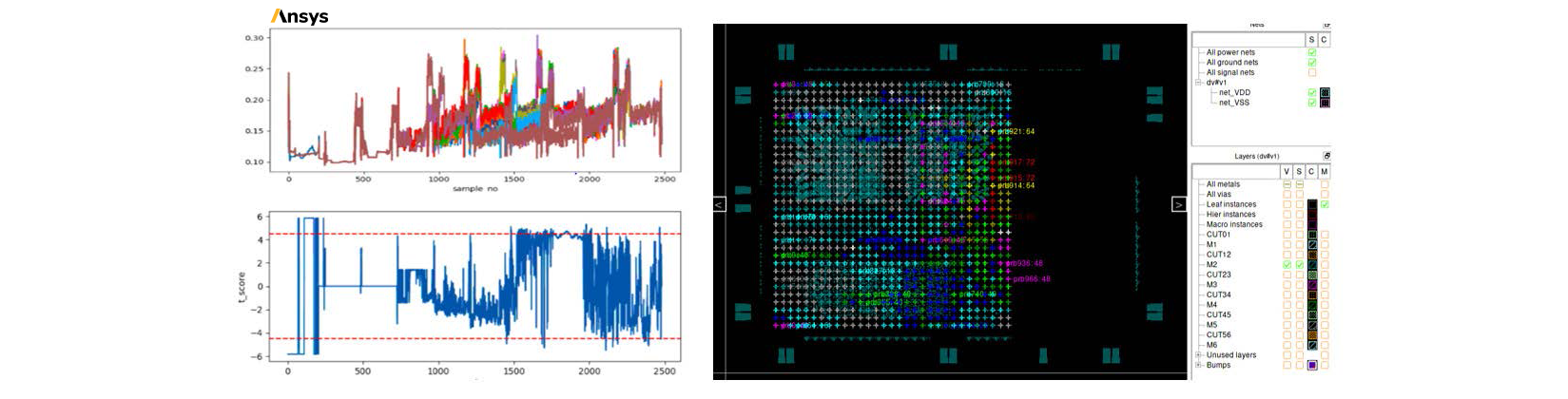 Virtually probe electromagnetic side-channels
Virtually probe electromagnetic side-channels
Revolutionizing hardware security
The collaboration between eShard and Ansys marks a significant shift in the way hardware security is approached. By integrating pre-silicon testing into the process, companies are no longer left scrambling to fix problems after production. Instead, they can proactively address side-channel vulnerabilities early, avoiding expensive redesigns and reducing the risk of delays.
As the stakes continue to rise in hardware security, combining the strengths of pre- and post-silicon testing offers a smarter, more resilient way forward. With eShard and Ansys working together, manufacturers can move confidently through every stage of chip design and production, knowing their products are secure, cost-effective, and ready to meet the challenges of an evolving threat landscape.
With eShard and Ansys working together, the future of hardware security is not just reactive — it’s proactive, comprehensive, and built to last.
Contact us for more information.